Cutting-Edge AI and Deep Learning Power the C² Data Privacy Platform
Our AI data privacy platform discovers and monitors sensitive data across all of your environments, providing clear insights into data exposure risks. With our intuitive interface, you can quickly understand vulnerabilities and take action to protect your clients’ and organization’s data.



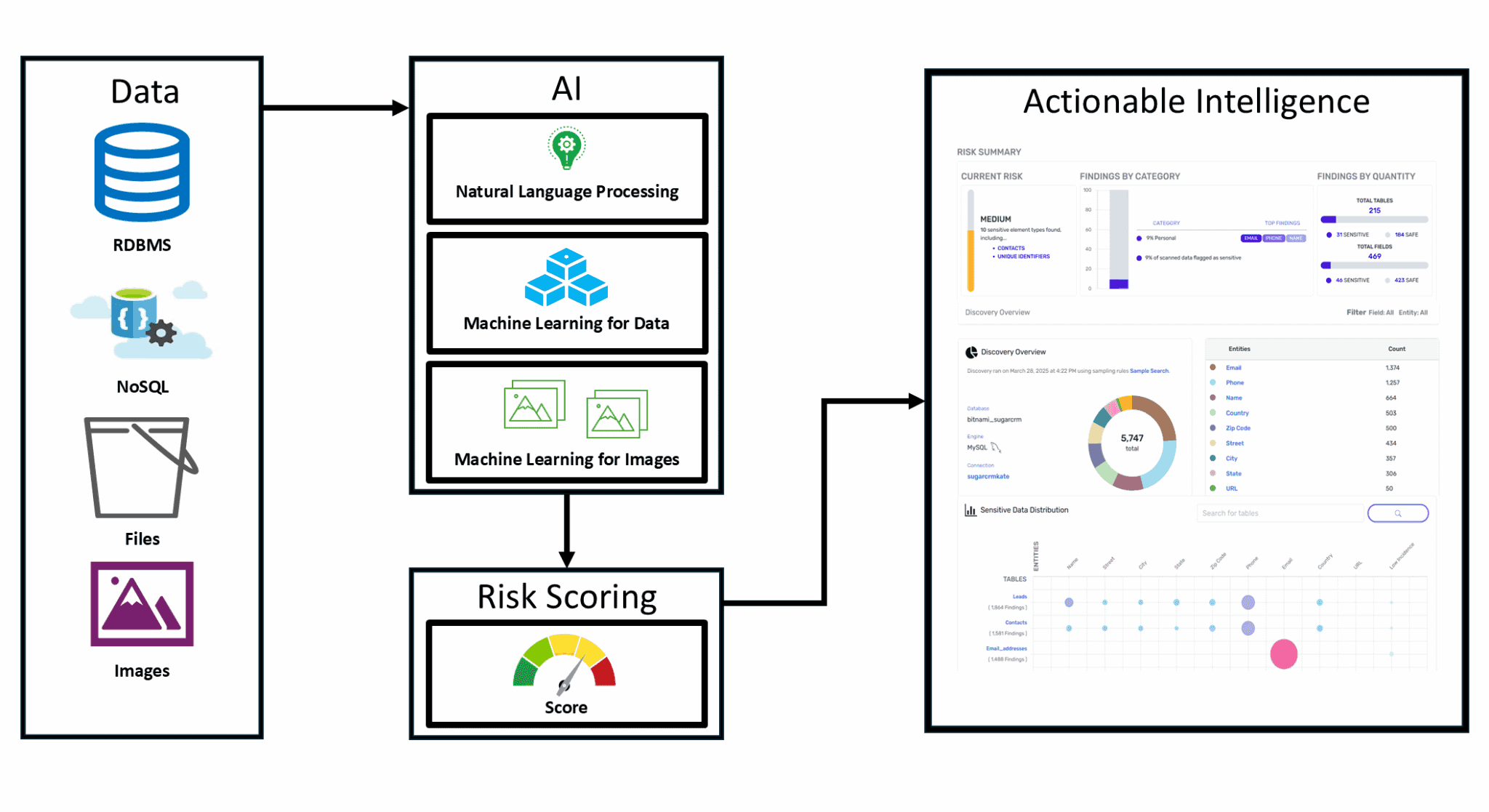

Discover, Secure, and Manage Data Seamlessly
AI Data Privacy
Our AI model offers context-based analysis, real-time monitoring and risk assessment.
AI Data Privacy
Our AI model offers context-based analysis, real-time monitoring and risk assessment.
Precision Discovery
Discover known and shadow data in structured and unstructured data.
Precision Discovery
Discover known and shadow data in structured and unstructured data.
Powerful Platform
A Data Security Posture Management solution built for the Cloud to manage all data in one platform.
Powerful Platform
A Data Security Posture Management solution built for the Cloud to manage all data in one platform.
AI Data Privacy
Our AI model offers context-based analysis, real-time monitoring and risk assessment.
Precision Discovery
Discover known and shadow data in structured and unstructured data.
Powerful Platform
A Data Security Posture Management solution built for the Cloud to manage all data in one platform.
Key Capabilities



01
03
Discover Sensitive Data
Discover Sensitive Data
C² Discover removes manual, error-prone sensitive data discovery processes and replaces it with AI-driven technology capable of discovering structured and unstructured data in minutes. C² Discover automates the sensitive data discovery process making it easy to reduce risk, quickly.
C² Discover removes manual, error-prone sensitive data discovery processes and replaces it with AI-driven technology capable of discovering structured and unstructured data in minutes. C² Discover automates the sensitive data discovery process making it easy to reduce risk, quickly.


Secure Sensitive Data
Secure Sensitive Data
C² Secure quickly and seamlessly secures sensitive data with a built-in encryption solution. Integrate existing data masking, data redaction, and synthetic data solutions and ensure data privacy regulations like HIPAA, CCPA, GDPR, GLBA are always met.
C² Secure quickly and seamlessly secures sensitive data with a built-in encryption solution. Integrate existing data masking, data redaction, and synthetic data solutions and ensure data privacy regulations like HIPAA, CCPA, GDPR, GLBA are always met.


Manage Sensitive Data
Manage Sensitive Data
C² Manage identifies EC2 instances, RDS, and S3 buckets across all AWS regions. Easily control costs with a toggle to turn data sources off and on as needed.
C² Manage identifies EC2 instances, RDS, and S3 buckets across all AWS regions. Easily control costs with a toggle to turn data sources off and on as needed.


CREW
Our Experts
We’ve spent 25 years in the trenches of data privacy and security, and one thing is clear: you cannot protect what you cannot see.
CREW
Our Experts
We’ve spent 25 years in the trenches of data privacy and security, and one thing is clear: you cannot protect what you cannot see.

George Barroso
Career-long systems whisperer who never met a legacy database he couldn’t tame. Spent 25+ years stitching together security, privacy, and performance in environments where downtime is not an option. Lives at the intersection of architecture diagrams and incident runbooks, making sure sensitive data stays visible to the right people and invisible to everyone else.
CIO

George Barroso
Career-long systems whisperer who never met a legacy database he couldn’t tame. Spent 25+ years stitching together security, privacy, and performance in environments where downtime is not an option. Lives at the intersection of architecture diagrams and incident runbooks, making sure sensitive data stays visible to the right people and invisible to everyone else.
CIO

Michael Logan
Recovering operator turned data evangelist. Two decades wrangling regulated data sets, cloud migrations, and grumpy auditors. Builder of products that let enterprises move fast on AI without waking up in front-page breach headlines. Still believes the right privacy architecture can turn “no” into “now” for the business.
CEO

Michael Logan
Recovering operator turned data evangelist. Two decades wrangling regulated data sets, cloud migrations, and grumpy auditors. Builder of products that let enterprises move fast on AI without waking up in front-page breach headlines. Still believes the right privacy architecture can turn “no” into “now” for the business.
CEO

Kris Glover
Hands-on architect with a bias for shipping secure-by-design systems, not just slideware. Veteran of large-scale cloud deployments where sensitive data hides in all the places scanners forget to look. Part machine-learning tinkerer, part threat-modeling purist, dedicated to building an AI-driven privacy platform that actually keeps up with how fast your engineers ship code.
Principal Architect

Kris Glover
Hands-on architect with a bias for shipping secure-by-design systems, not just slideware. Veteran of large-scale cloud deployments where sensitive data hides in all the places scanners forget to look. Part machine-learning tinkerer, part threat-modeling purist, dedicated to building an AI-driven privacy platform that actually keeps up with how fast your engineers ship code.
Principal Architect
BLOG
Data Privacy Articles
BLOG
Data Privacy Articles
ENTERPRISE SOFTWARE
C² Data Privacy Platform Delivers

ENTERPRISE SOFTWARE
C² Data Privacy Platform Delivers

Full, AI-driven visibility into sensitive data across all environments.
Proactive risk reduction through continuous discovery, classification, and scoring.
Ability to safely accelerate AI and cloud initiatives without slowing the business down.
Full, AI-driven visibility into sensitive data across all environments.
Proactive risk reduction through continuous discovery, classification, and scoring.
Ability to safely accelerate AI and cloud initiatives without slowing the business down.
ABOUT US
GET IN TOUCH
ABOUT US
GET IN TOUCH







